We use machine learning technology to do auto-translation. Click "English" on top navigation bar to check Chinese version.
Automated Security Monitoring for RISE with SAP and SAP BTP on Amazon Web Services
This blog was co-authored by Amos Wendorff, Senior Cyber Security Design Specialist at SAP
Introduction:
At Amazon Web Services, we are committed to providing our customers with robust security solutions that enable them to use cloud services with confidence. In this post, we’ll explore SAP provide secure and compliant RISE with SAP and SAP BTP (Business Technology Platform) environments running on Amazon Web Services for their customers, and how they have implemented an automated solution for security monitoring and alerting using Amazon Web Services Services.
RISE with SAP is a comprehensive offering that provides businesses with a path to transform their Enterprise Resource Planning (ERP) systems and migrate to the cloud. It combines SAP’s intelligent enterprise software with cloud infrastructure and services, allowing customers to simplify their IT landscapes, innovate faster, and drive digital transformation. By adopting RISE with SAP, customers can leverage the power of SAP applications, such as SAP S/4HANA, while benefiting from the scalability, security, and cost-efficiency of the cloud.
Background:
The number of Amazon Web Services accounts used by SAP has grown exponentially due to the rapid adoption of RISE with SAP and SAP BTP. SAP currently operates in 33 Amazon Web Services regions and is expanding to new regions as they launch, managing over 7,000 Amazon Web Services accounts, at the time of publication of the blog post. Manually monitoring and securing these numerous accounts would be an immense challenge. To address this, SAP required a scalable, secure, and automated solution that could scale with their customers’ needs while leveraging Amazon Web Services’s robust security services.
Technical Implementation:
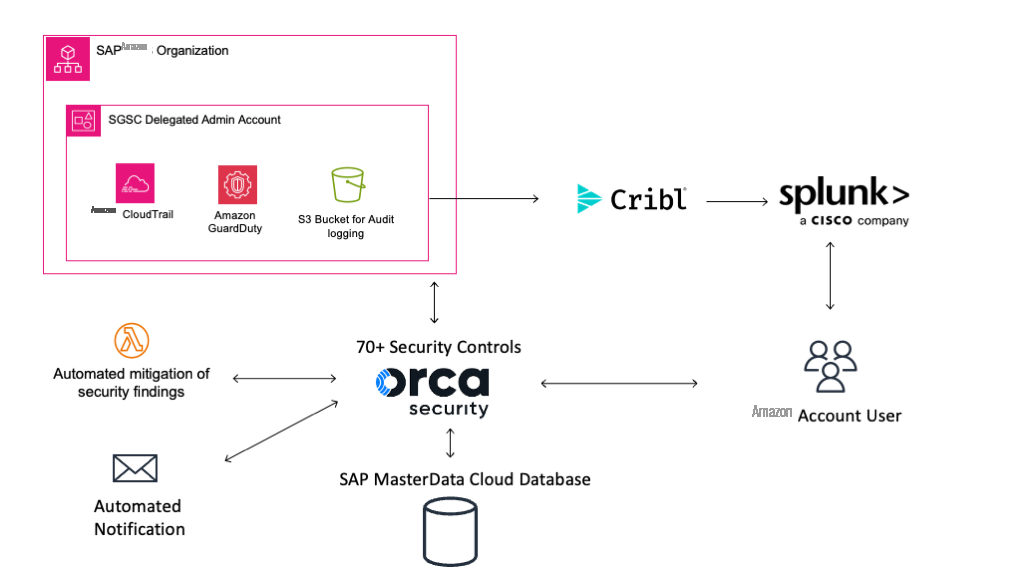
SAP’s Global Security & Cloud Compliance (SGSC) team has built a robust “Secure by Default” framework that leverages a combination of Amazon Web Services services and third-party tools to ensure comprehensive security across more than 7,000 Amazon Web Services accounts. At the heart of this architecture is Amazon GuardDuty, which provides continuous monitoring of Amazon Web Services environments for malicious or unauthorized activities. Amazon GuardDuty integrates seamlessly with Amazon Web Services, utilizing machine learning, anomaly detection, and threat intelligence to deliver real-time threat detection. All Amazon GuardDuty findings and security logs are aggregated in Amazon S3, which acts as a central repository for logs across the Amazon Web Services Organization. This setup allows SAP to maintain visibility and control over its vast cloud infrastructure.
To handle the high volume of data, SAP employs Cribl to process logs by filtering, enriching, and normalizing them before routing to destinations like Splunk for advanced analysis and visualization. This ensures that the security team can efficiently manage and analyze the data, identifying and responding to threats quickly. SAP also maintains a MasterData Cloud Database that holds metadata for each Amazon Web Services account, including contact information for account owners and security operators, enabling targeted notifications and responses when security issues are detected. This is crucial for maintaining clear accountability and rapid response capabilities.
In addition to detection and analysis, SAP uses Amazon Lambda functions to automate the remediation of specific security findings. For example, if GuardDuty flags an open port that violates security policies, an Amazon Lambda function is triggered to automatically remediate the issue, by adjusting security group rules. This automation reduces the need for manual intervention and ensures compliance across all Amazon Web Services accounts. For RISE with SAP and SAP BTP customers, whose environments are operated by SAP, this architecture ensures that their cloud resources are continuously monitored and protected under these stringent security controls, providing peace of mind and operational continuity.
Overall, SAP’s approach integrates Amazon Web Services-native security capabilities with advanced data processing tools to create an automated, scalable, and secure cloud environment, tailored specifically for the needs of SAP applications on Amazon Web Services.
Overview of Security Controls:
SAP’s “Secure by Default” controls encompass various measures to ensure a secure cloud environment by leveraging Amazon Web Services’s native security capabilities. These include enforcing all accounts into the Amazon Web Services organization for uniform policy application, integration with SAP Active Directory, preventing non-SAP domain users, and mandatory MFA for cloud administrators. Centralized logging is applied across all accounts, ensuring that API audit logs and storage access logs cannot be deactivated and are continuously ingested into the SIEM (Security Information and Event Management). This approach not only protects against common cloud misconfigurations, like publicly accessible resources or unencrypted data, but also utilizes Amazon Web Services’s organizational governance features to enforce advanced network controls such as block-listing specific ports and enforcing TLS 1.2+ for secure communications.
Phased Rollout Using Deployment Rings:
New preventive controls are rolled out in four deployment rings. This staggered approach allows teams to test policies and minimize disruption. Account owners can choose their account placement in the deployment rings and receive at least two weeks’ notice before policy enforcement. SAP considers potential disruptions and contemplates exceptions or delays for specific controls to ensure minimal impact.
Notification and Remediation Process:
The automated security monitoring triggers a notification process based on the severity of the detected control violation. High-severity alerts are automatically remediated through SAP’s automation processes, leveraging Amazon Lambda.
Automated Account Provisioning and Security Standards:
SAP’s automated account provisioning process ensures that each new Amazon Web Services account adheres to predefined security standards and best practices from the outset. This includes implementing required IAM roles, Amazon Web Services security tools, and compliance with SGSC security policies.
The process involves a sophisticated vending system that manages the automated lifecycle of accounts. The first layer of security is implemented through Service Control Policies (SCPs), which block specific actions and resources. Detection mechanisms are put in place using Amazon GuardDuty and Amazon CloudTrail. Orca Security enhances SAP’s cloud security posture through automated, agentless scanning and remediation of vulnerabilities, misconfigurations, and compliance risks. By embedding security directly into the SAP Amazon Web Services full Organization, SAP adopts a proactive approach to identifying and mitigating risks early in the lifecycle. This integration ensures a robust security foundation for customer workloads, minimizing attack surfaces and aligning with best practices for cloud-native environments.
In addition to the standard security measures, SAP leverages several Amazon Web Services features to enhance the security of RISE with SAP environments at the account level:
- EBS Snapshot Lock used for Backups for RISE with SAP: To better protect its clients’ data, SAP adopted Amazon Elastic Block Store (Amazon EBS) Snapshot Lock. This feature locks new and existing Amazon EBS Snapshots using a lock duration that can range from 1 day to about 100 years. This protects stored data from being unintentionally deleted, providing SAP’s enterprise customers with greater peace of mind. SAP uses the Amazon Data Lifecycle Manager to automate the creation, retention, and deletion of snapshots based on predefined schedules and retention guidelines. Then, it uses Amazon EBS Snapshot Lock to secure these backups under stringent compliance controls. The feature’s compliance mode verifies that the snapshots cannot be deleted, even by authorized users. After an optional cooling-off period of up to 72 hours, neither the snapshot nor the lock can be deleted until the lock duration expires, and the mode cannot be changed. SAP’s customers also have the option of customizing how long they would like to lock their snapshots, which has ranged from a few weeks to up to 2 years.
- Bring Your Own Key (BYOK) for RISE with SAP: Customers can enhance security by using their own Amazon KMS customer master key (CMK) to encrypt data in their RISE with SAP environment. By creating a CMK in the same region and granting RISE with SAP Amazon Web Services account permission, customers can leverage their key for encrypting EFS, data volumes, and backups. This approach provides greater control over data encryption, allows key access revocation, and ensures cryptographic requirements are met, all while benefiting from Amazon KMS’s 99.999% availability SLA.
- Amazon WAF for RISE with SAP: Amazon WAF (Web Application Firewall) is an integral security component of RISE with SAP environments, providing automatic protection for web applications and APIs against common web exploits, and resource abuse through geo-blocking. Automated deployment and configuration during environment provisioning ensure consistent protection without requiring customer intervention. This setup delivers enterprise-grade web application security, enhancing the overall security posture of RISE with SAP environments.
- Mutual TLS (mTLS) Verification for Amazon Web Services Customers in RISE: Mutual TLS (mTLS) Verification is an advanced security feature available to Amazon Web Services customers within the RISE with SAP environment. This feature provides an additional layer of authentication and security for network communications, offering enhanced protection for sensitive workloads and applications. The key benefits of mTLS include enhanced security through stronger authentication than traditional TLS, client verification to ensure that only authorized clients can connect to your services, and data integrity through the maintenance of confidentiality and integrity of data in transit. Furthermore, mTLS helps meet strict regulatory requirements in industries such as finance and healthcare, ensuring compliance with relevant standards. By incorporating mTLS, RISE with SAP customers benefit from a highly secure and compliant cloud environment, further enhancing the overall security posture of their applications and workloads.
- SAP BTP Private Link for RISE with SAP: SAP BTP Private Link, a service based on Amazon PrivateLink, establishes a secure, private network connection between SAP BTP and RISE with SAP environment, routing traffic through Amazon Web Services’s internal network and eliminating public internet exposure while maintaining low-latency, high-performance communication.
Benefits of the Automated Solution:
- Enhanced Security Posture: Real-time detection and alerting of security violations enable quick action and prevent security incidents.
- Scalability: Scales security controls across thousands of Amazon Web Services accounts, ensuring comprehensive coverage and protection.
- Automation: Automated security monitoring reduces the need for manual interventions and increases the efficiency of SAP’s security operations.
For organizations looking to implement a similar approach, a key starting point is to adopt a cloud-native mindset and fully utilize Amazon Web Services’s built-in security features. This includes setting up Amazon Organizations to manage accounts centrally, applying service control policies (SCPs) for security guardrails. By using cloud-native tools such as Amazon GuardDuty for threat detection, Amazon CloudTrail for audit logging, and Amazon Key Management Service (KMS) for secure key management, organizations can build a Zero Trust Architecture that significantly reduces their attack surface and enhances overall security posture. Ensuring encryption standards, enforcing password policies, and enabling MFA at all access points are practical steps to follow. For a comprehensive guide on implementing these security best practices, organizations should refer to the Amazon Web Services Well-Architected Framework’s Security Pillar documentation . Additionally, specific guidance on leveraging Amazon Web Services Security Services alongside RISE with SAP can be found in the Amazon Web Services Security Considerations for RISE with SAP.
Conclusion:
By adopting a cloud-native security strategy that leverages Amazon Web Services’s robust security services, automation capabilities, and organizational policy engines, SAP’s “Secure by Default” solution allows customers using RISE with SAP, SAP BTP, and other SAP solutions on Amazon Web Services to focus on their core business objectives with confidence in their security posture. This approach integrates the principles of Zero Trust Architecture (ZTA), where continuous validation of user access, strict governance of cloud resources, and enforced compliance through Amazon Web Services-native tools are paramount. SAP minimizes risks by employing real-time detection through, alert and automated remediation. This enables SAP customers to maximize the value of their cloud investments, assured that their sensitive data and workloads are safeguarded by SAP’s comprehensive and scalable security framework on Amazon Web Services.
The mentioned AWS GenAI Services service names relating to generative AI are only available or previewed in the Global Regions. Amazon Web Services China promotes AWS GenAI Services relating to generative AI solely for China-to-global business purposes and/or advanced technology introduction.

















