We use machine learning technology to do auto-translation. Click "English" on top navigation bar to check Chinese version.
Configuring KMS encryption at rest on ECR repositories with ECR replication
Introduction
In this blog post, you’ll learn how to configure
Customers in environments that are sensitive to compliance and regulatory concerns often want to enable encryption whenever possible. Enterprises want to secure their data footprints in transit and at rest, and container images are no exception to this posture.
With Amazon Web Services KMS and Amazon ECR image replication, we can transfer the images across
Architecture
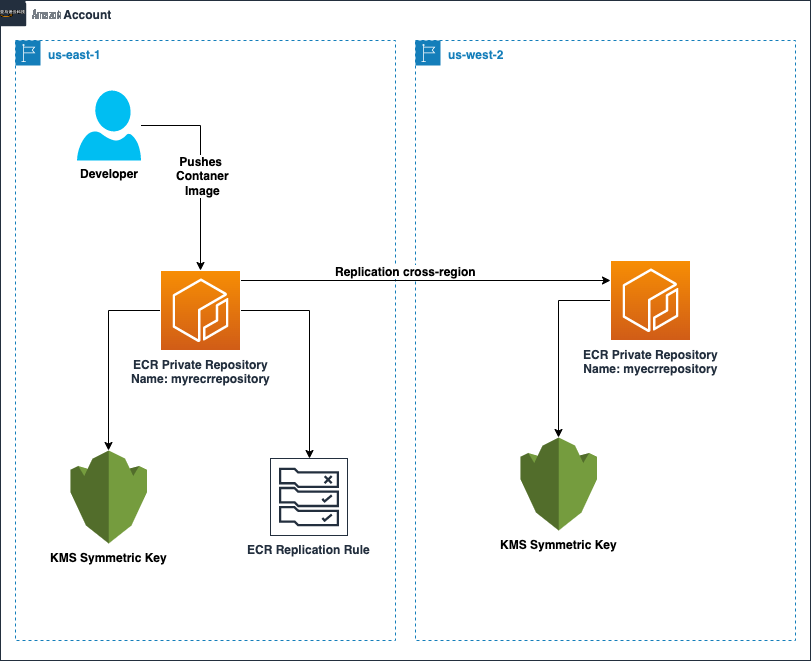
For cross-Region replication, below is the diagram for our solution:
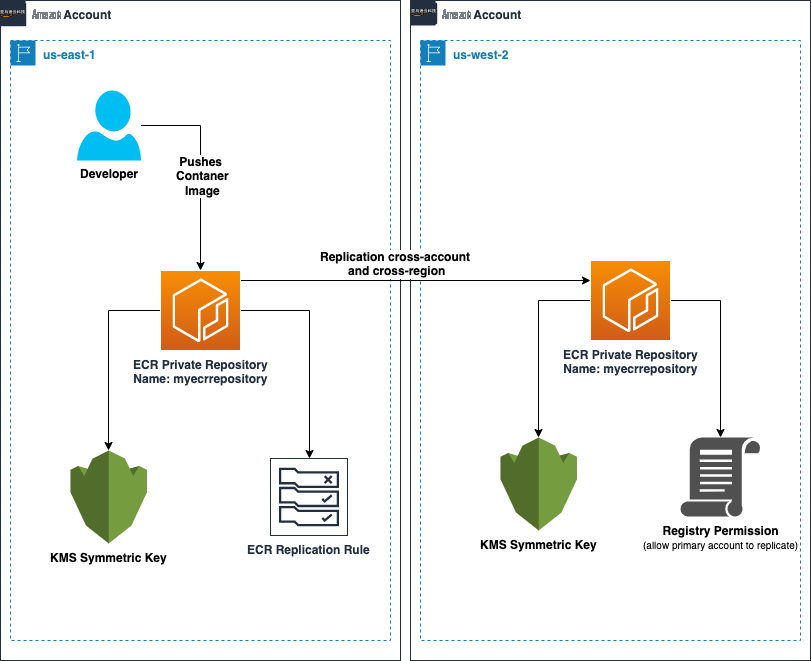
The following diagram shows our solution for cross-Region and cross-account replication:
Walkthrough
| Time to read | 5 mins |
| Time to complete | 10 mins |
| Cost to complete |
~$5 per month (for two Regions)
|
| Learning level | Intermediate (200) |
| Services used | Amazon Elastic Container Registry (ECR) and Amazon Web Services Key Management Service (KMS) |
Amazon ECR with Amazon Web Services KMS encryption cross-Region replication
Following is an example of creating replication between two Amazon ECR repositories in two different Regions with Amazon Web Services KMS encryption enabled. The order of the steps is crucially important. Please do not run the steps out of order.
To create an Amazon Web Services KMS key in the primary Region
- Open the Amazon Web Services KMS console in the desired primary Region (for example, N. Virginia.
- Choose Create Key .
- Select Symmetric key type.
- Select Encrypt and decrypt key usage.
- Choose Next .
- Enter an Alias for your Amazon Web Services KMS key (for example, “ECR KMS Key”).
- Choose Next .
- In the Define key administrative permissions field , choose an IAM user or role.
- Choose Next .
-
In the
Define key usage permission
field, choose an IAM user and/or role.
- Make sure your IAM user or role is also selected. This will be required for Amazon ECR to encrypt and decrypt the container image.
- Choose Next .
- Choose Finish .
To create an Amazon ECR repository in the primary Region
- Open the Amazon ECR console in the desired primary Region (for example, N. Virginia)
- Choose Get Started .
- Choose Private as visibility settings.
- Enter your Repository Name (i.e., myrepo).
-
In the
Encryption Settings
section, do the following:
- Enable encryption .
- Choose Customize encryption settings (advanced) .
- Choose the key we just created in the steps above.
- Choose Create repository .
At this point, you have an Amazon ECR repository created with Amazon Web Services KMS encryption enabled. Before enabling Amazon ECR replication, let’s create the Amazon ECR repository in the secondary Region.
To create the Amazon Web Services KMS repository in the second Region
- Open the Amazon Web Services KMS console in the desired secondary Region (for example, Oregon).
- Choose Create Key .
- Select Symmetric key type.
- Select Encrypt and decrypt key usage.
- Choose Next .
- Enter an Alias for your Amazon Web Services KMS key (i.e., “ECR KMS Key”).
- Choose Next .
- In the Define key administrative permissions field, choose an IAM user or role.
- Choose Next .
-
In the
Define key usage permission
field, choose an IAM user or role.
- Make sure your IAM User or role is also selected. This will be required for Amazon ECR to encrypt and decrypt the container image.
- Choose Next .
- Choose Finish .
To create an Amazon ECR repository in the primary Region
- Open the Amazon ECR console in the desired secondary Region (for example, Oregon).
- Choose Get Started .
- Choose Private for the visibility settings.
-
Enter your
Repository Name
(for example, myrepo).
- It’s very important that you give the same repository name as in your primary Region. If repository names between primary and replicated Regions do not match, replication will fail.
-
In the
Encryption settings
section, do the following:
- Enable encryption .
- Choose Customize encryption settings (advanced) .
- Choose the key we just created in the previous steps.
- Choose Create repository .
If you would like to replicate the Amazon ECR repositories to other Regions, repeat the steps for the secondary Region on the desired Region.
Finally, let’s enable the Amazon ECR replication configuration.
To enable Amazon ECR replication
- Open the Amazon ECR console in the primary Region (for example, N. Virginia.
- In the navigation pane, choose Private registry , then choose Replication configuration and press Edit .
- Choose Add rule .
- Choose Cross-region replication for replications between Regions.
- Choose Next .
- Choose the Destination Regions(s) that you created in your secondary Amazon ECR repository(s) (for example, Oregon).
- Choose Next .
-
In the
Repository filters,
do the following:
- Enter the repository name (for example, myrepo). It needs to match exactly with the repository name you created.
- Choose Add .
- Choose Next .
- Choose Submit rule .
(Optional) Amazon ECR with Amazon Web Services KMS encryption cross-account replication
(Optional) If you would like to enable cross-account replication, follow all the steps above with the secondary/destination Region to another Amazon Web Services account, utilizing Amazon ECR replication we will need to create the cross-Region replication. Additionally, you will need to create an Amazon ECR replication rule and permission on the destination account.
(Optional) To enable a cross-account replication rule
- Open the Amazon ECR console in the primary Region (for example, N. Virginia).
- In the navigation pane, choose Private Registry , then choose Replication .
- Choose Add rule .
- Choose Cross-account replication for replications between accounts.
- Choose Next .
- Choose the destination account that you created your secondary Amazon ECR repository(s).
- Choose the destination Regions that you would like Amazon ECR to replicate to the secondary Amazon Web Services account.
- Choose Next .
-
In the
Repository filters
, do the following:
- Enter the repository name (for example, myrepo). It needs to match exactly with the repository name you created.
- Choose Add .
- Choose Next .
- Choose Submit rule .
(Optional) To enable cross-account replication permission
- Open the Amazon ECR console in the secondary Region (for example, Oregon) in the other Amazon Web Services account.
- In the navigation pane, choose Private Registry , then choose Permission .
- Choose Cross account replication policy in the Policy type.
- Enter a Statement id (for example, “replication cross-account policy”).
- In the Accounts section, enter the Amazon Web Services account number where the primary Amazon ECR repository resides.
- Choose Save statement .
-
The console will autogenerate a JSON IAM policy similar to the following:
Finally, you should be able to push an image into your primary account Amazon ECR repository, and automatically the image will be replicated to your secondary Amazon ECR account.
CloudFormation automation
The same solution can be achieved by deploying CloudFormation infrastructure-as-code (IaC) templates. These templates with instructions can be found in our
The repository contains two solutions:
- Cross-Region replication (same account)
- Cross-Region and Cross-account replication
Conclusion
In summary, we’ve described how you can enable encryption in transit for container images stored in Amazon ECR by using Amazon Web Services KMS keys for image transfer between Regions or accounts.
We’ve reviewed the components involved and how they function together for secure transfer of the container image. Furthermore, we have successfully automated the functionality described allowing you to quickly enable the services in your own Regions and accounts.
If you have feedback about this post, please submit it in the comments section below. If you have questions about this post, please start a new thread on the
The mentioned AWS GenAI Services service names relating to generative AI are only available or previewed in the Global Regions. Amazon Web Services China promotes AWS GenAI Services relating to generative AI solely for China-to-global business purposes and/or advanced technology introduction.