We use machine learning technology to do auto-translation. Click "English" on top navigation bar to check Chinese version.
Identifying IoT device certificates with a revoked intermediate CA using Amazon Web Services IoT Device Defender
Introduction
Dynamically verifiable device identity is a
Background
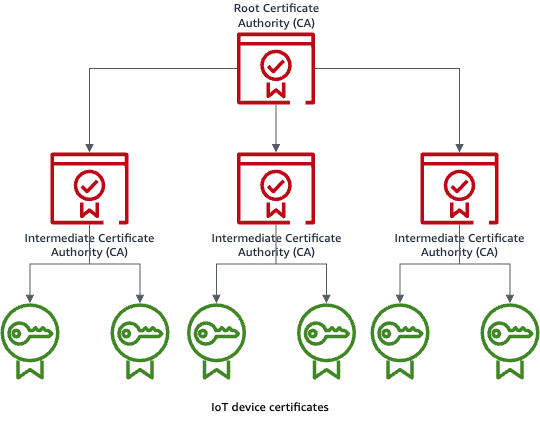
Figure 1. Hierarchical public key infrastructure (PKI) chain including root CA, intermediate CA, and IoT device certificates issued by an intermediate CA.
In most practical applications, intermediate CAs issue device certificates as this approach
Previously, Amazon Web Services IoT Core customers who
Solution
Customers using their own device certificates needed an automated mechanism to identify certificates with a revoked intermediary CA. With the new
The new check makes it easier for customers to identify affected certificates using relevant X.509 certificate extension declarations and
How to identify active device certificates with a revoked intermediate CA
The new audit check leverages standard revocation check methods whilst being able to traverse public key infrastructure (PKI) hierarchies. It relies on the information provided via relevant X.509 certificate extensions to discover the PKI CA hierarchy and perform the associated certificate revocation checks.
In our sample scenario shown in Figure 2, this audit check occurs as the following sequence:
- Root CA or intermediate CA revokes the target intermediate CA certificate, where the intermediate CA is the issuer of a certificate actively used by an IoT device interacting with Amazon Web Services IoT Core.
- Customer initiates an Amazon Web Services IoT Device Defender audit, which includes the revoked intermediate CA audit check.
- Amazon Web Services IoT Device Defender performs the revocation check using the available revocation check method, in accordance with the hierarchy of the associated PKI.
- If a revoked intermediate CA is identified, the audit generates a non-compliant “Intermediate CA revoked for active device certificates” finding.

Figure 2. Amazon Web Services IoT Device Defender revoked intermediate CA audit check flow.
To use this feature, you can access the
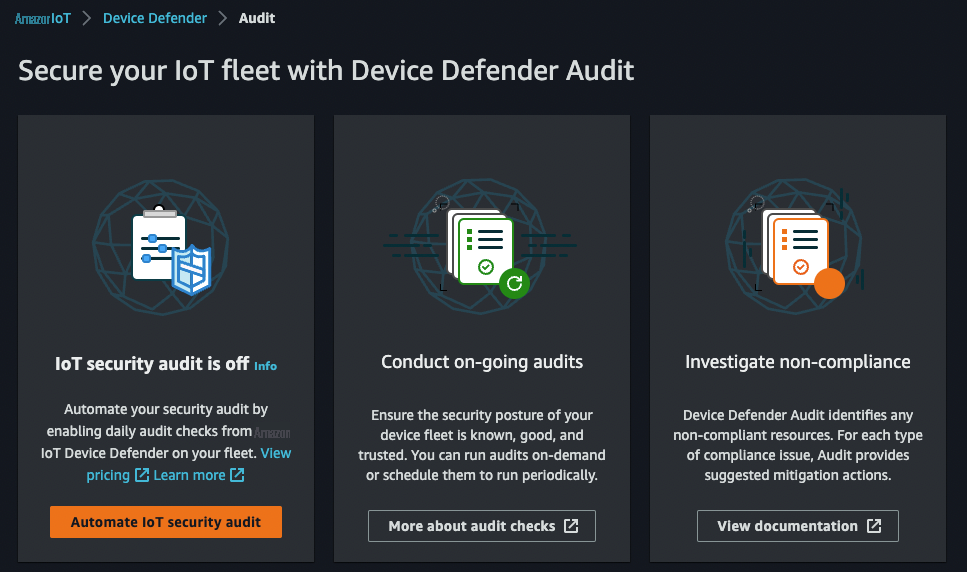
Figure 3. Amazon Web Services IoT Device Defender audit section.
The check handles device certificates that have an issuer endpoint declared in the relevant X.509 extension, and reports active certificates issued by a revoked intermediate CA. You can disable the compromised device certificate using a pre-built mitigation action or initiate a custom mitigation through an Amazon Web Services Lambda function. More documentation on Amazon Web Services IoT Device Defender intermediate CA audit check can be
Customer device certificates used with Amazon Web Services IoT Core need to include the necessary Authority Information Access (AIA) details required to perform the underlying CA revocation checks:

Figure 4. X.509 certificate extension declarations showing certificate Authority Information Access (AIA) and CRL endpoint details.
Subsequently, the Intermediate CA revoked for active device certificates audit check can be used to identify any active device certificates issued by the revoked intermediate CA.
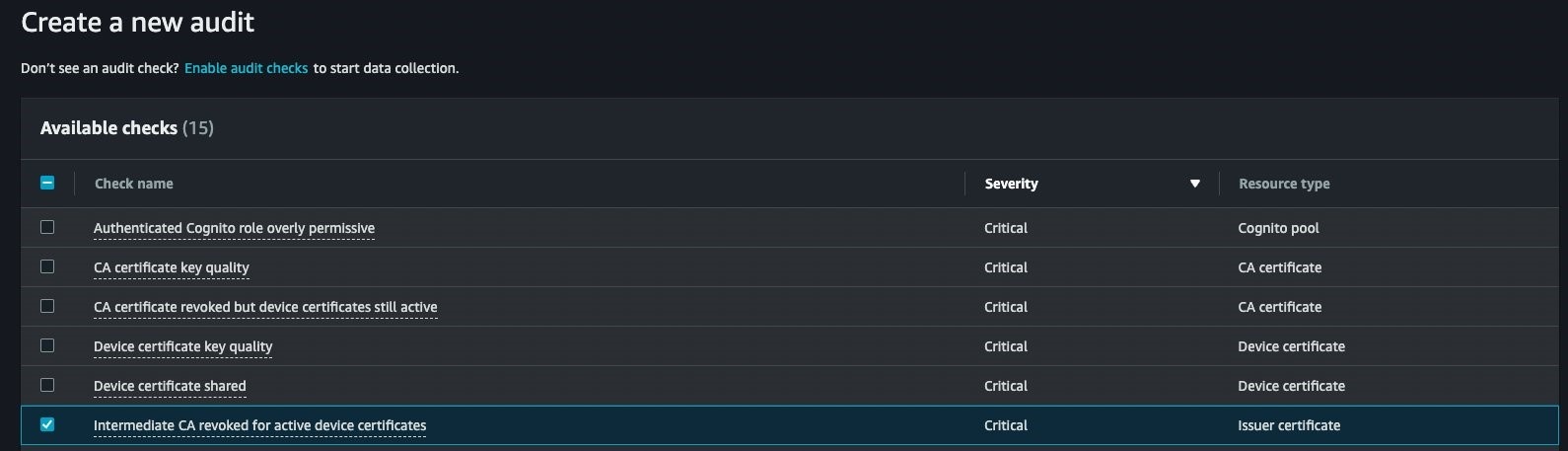
Figure 5. Selecting the Intermediate CA revoked for active device certificates audit check as part of new audit creation process.
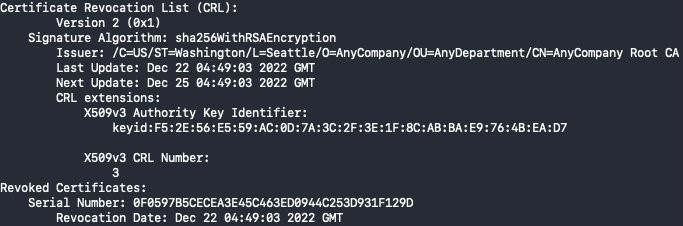
The check can leverage the AIA details and published certificate revocation information, whilst traversing the associated PKI hierarchy to determine the intermediate CA revocation status. In this test example, we can see that an intermediate CA used to issue device certificates was revoked by the root CA:
 .
.
Figure 6. Example Certificate Revocation List (CRL) entry showing a revoked certificate corresponding to the intermediate CA.
Upon revocation, a previously compliant audit check would fail, because Amazon Web Services IoT Device Defender identifies a revoked intermediate CA.
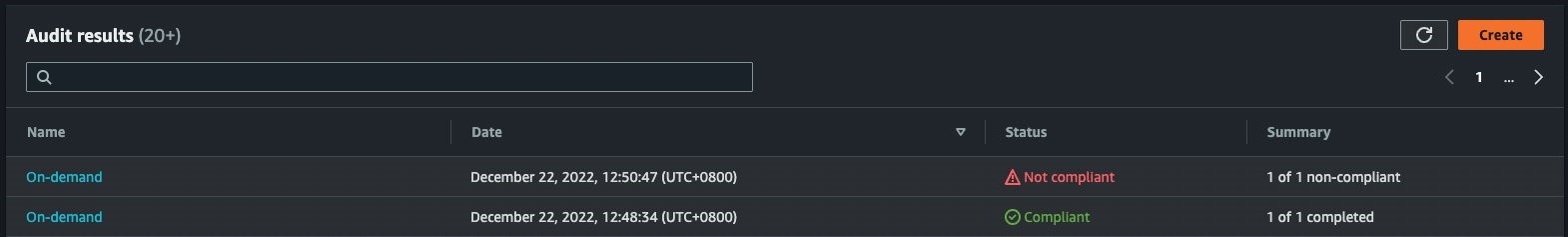
Figure 7. Amazon Web Services IoT Device Defender Audit Result showing non-compliant audit finding.
The associated finding provides additional information about the impacted device certificates, as well as the affected issuer identifier registered with Amazon Web Services IoT Core.

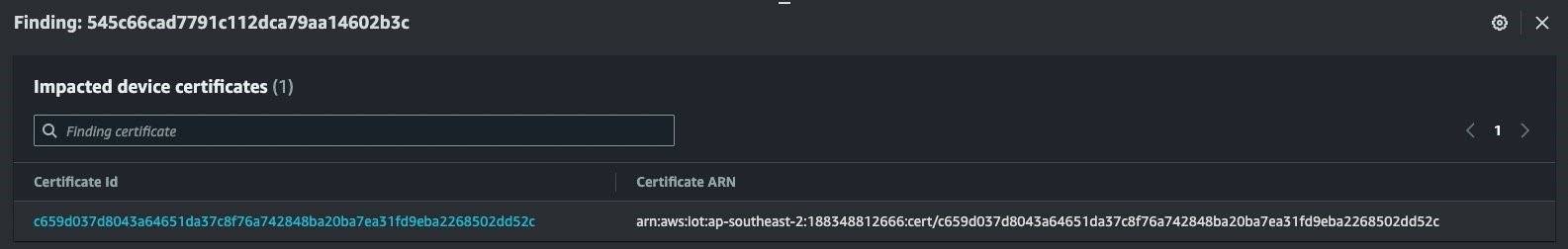
Figure 8. Additional information provided as part of the associated Intermediate CA revoked for active device certificates audit finding.
You can now identify client or device certificates that have their issuing CA revoked in a CA chain via a scheduled audit automatically, or initiate an ad-hoc Amazon Web Services IoT Device Defender audit report manually as needed.
If non-compliant certificates are identified, you can initiate a pre-built mitigation action, such as disabling the affected device certificate or initiate a custom mitigation action through a Lambda function.
Conclusion
IoT devices using device certificates issued by a revoked intermediate CA can pose a security threat to your IoT solution. Amazon Web Services recommends identifying active devices issued by a revoked intermediate CA and taking actions such as disabling or replacing these device certificates.
This recommendation aligns with one of the core principles of ZTA of continuously monitoring and measuring the integrity and security posture of your IoT devices and verifying device trust on an ongoing basis.
Using the new Amazon Web Services IoT Device Defender audit check feature, customers can continuously audit, monitor, and remediate affected device identities, such as:
- Provision new certificates, that are signed by a different CA, for the affected devices.
- Verify that the new certificates are valid, and that the devices can use them to connect.
-
Initiate built-in Amazon Web Services IoT Device Defender
mitigation actions or custom mitigation actions through a Lambda function, if required. Customers can perform these mitigation actions by calling theAmazon Web Services IoT Device Defender API orAmazon Web Services CLI directly.
The new audit check makes it easier for customers to identify affected certificates, helping to improve the overall security posture of your IoT solutions.
Authors
The mentioned AWS GenAI Services service names relating to generative AI are only available or previewed in the Global Regions. Amazon Web Services China promotes AWS GenAI Services relating to generative AI solely for China-to-global business purposes and/or advanced technology introduction.