We use machine learning technology to do auto-translation. Click "English" on top navigation bar to check Chinese version.
Improve security of Amazon RDS master database credentials using Amazon Web Services Secrets Manager
Amazon RDS now offers integration with Secrets Manager to manage master database credentials. You no longer have to manage master database credentials, such as creating a secret in Secrets Manager or setting up rotation, because Amazon RDS does it for you.
In this blog post, you will learn how to set up an Amazon RDS database instance and use the Secrets Manager integration to manage master database credentials. You will also learn how to set up alternating users rotation for application credentials.
Benefits of the integration
Managing Amazon RDS master database credentials with Secrets Manager provides the following benefits:
- Amazon RDS automatically generates and helps secure master database credentials, so that you don’t have to do the heavy lifting of securely managing credentials.
- Amazon RDS automatically stores and manages database credentials in Secrets Manager.
- Amazon RDS rotates database credentials regularly without requiring application changes.
- Secrets Manager helps to secure database credentials from human access and plaintext view.
- Secrets Manager allows retrieval of database credentials using its API or the console.
-
Secrets Manager allows fine-grained control of access to database credentials in secrets using
Amazon Web Services Identity and Access Management (IAM) . -
You can separate database encryption from credentials encryption with different
Amazon Web Services Key Management Service (Amazon Web Services KMS) keys. -
You can monitor access to database credentials with
Amazon Web Services CloudTrail andAmazon CloudWatch .
Walkthrough
In this blog post, we’ll show you how to use the console to do the following:
- Manage master database credentials for new Amazon RDS instances in Secrets Manager. We will use the MySQL engine, but you can also use this process for other Amazon RDS database engines.
- Use the managed master database secret to set up alternating users rotation for a new database user.
Manage Amazon RDS master database credentials in Secrets Manager
In this section, you will create a database instance with Secrets Manager integration.
To manage Amazon RDS master database credentials in Secrets Manager:
-
Open the
Amazon RDS console and choose Create database . - For Choose a database creation method , choose Standard create .
- In Engine options , for Engine type , choose MySQL .
-
In
Settings
, under
Credentials Settings
, select
Manage master credentials in Amazon Web Services Secrets Manager
.
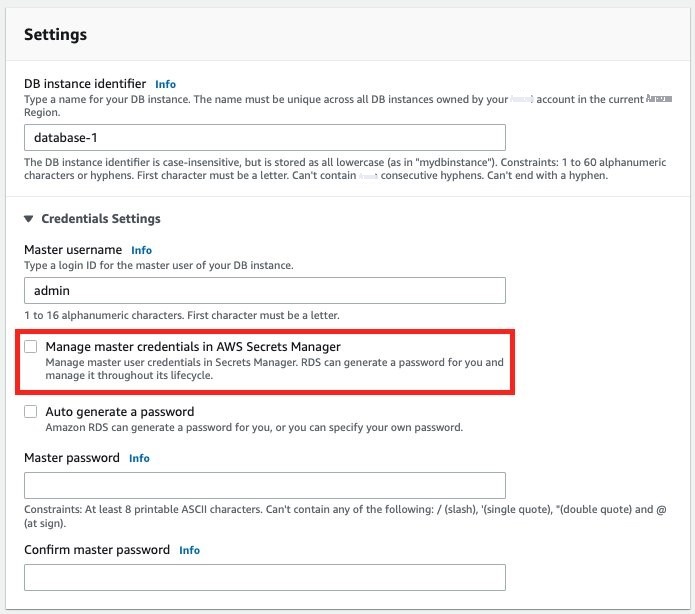
Figure 1: Select Secrets Manager integration
-
You will have the option to encrypt the managed master database credentials. In this example, we will use the default KMS key.
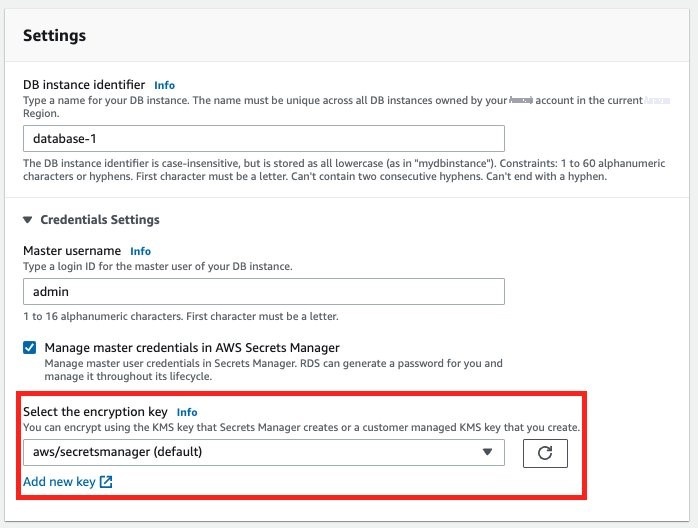
Figure 2: Choose KMS key
-
(Optional) Choose other settings to meet your requirements. For more information, see
Settings for DB instances . - Choose Create Database , and wait a few minutes for the database to be created.
- After the database is created, from the Instances dashboard in the Amazon RDS console, navigate to your new Amazon RDS instance.
- Choose the Configuration tab, and under Master Credentials ARN , you will find the secret that contains your master database credentials.
Create a new database user by using the master database credentials
In this section you will learn how to create and secure a credential that could be used in your application to connect to the database. You will learn how to access the master database credentials and use the master database credentials to create and set up rotation on child (application) credentials.
To create a new database user by using the master database credentials
-
Retrieve the master database credentials from Secrets Manager as follows:
-
Choose the
Configuration
tab of your RDS instance dashboard, and under
Master Credentials ARN
, choose
Manage in Secrets Manager
to open your managed master database secret in Secrets Manager.
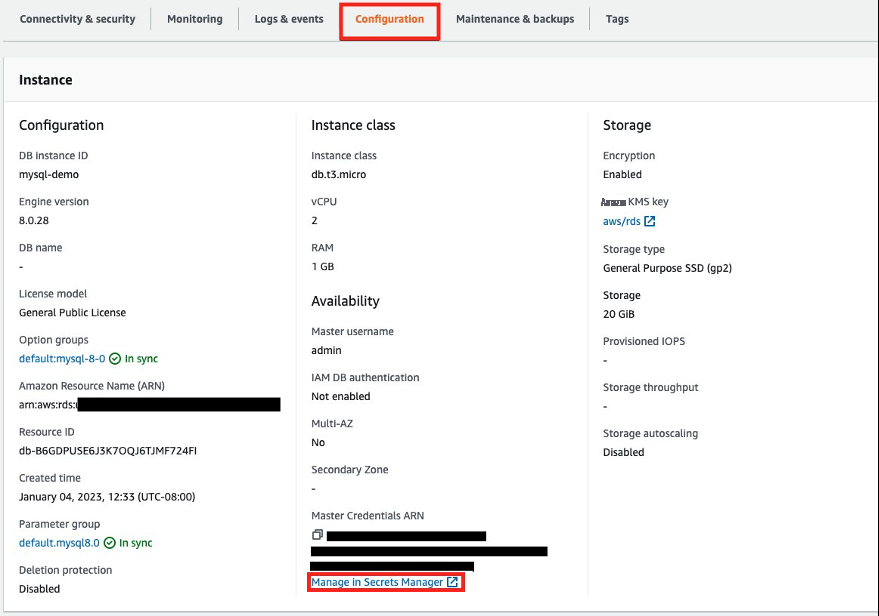
Figure 3: View DB configuration
-
You can see that Amazon RDS has added some system tags to the secret and that rotation is turned on by default.
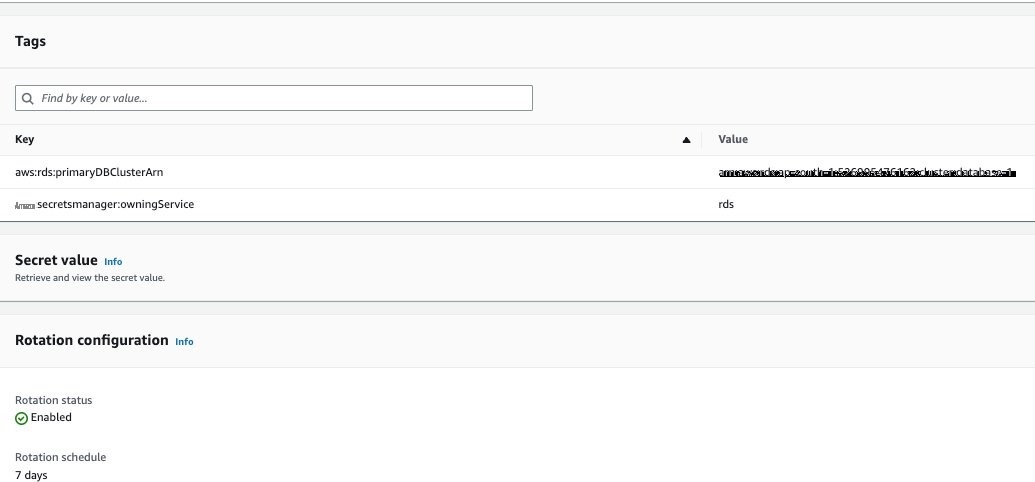
Figure 4: View secret details
- To see the password, in the Secret value section, choose Retrieve secret value .
Note : Your applications can retrieve these credentials by using the
Amazon Web Services Command Line Interface (Amazon Web Services CLI) orAmazon Web Services SDK if they have IAM permission to read the secret. -
Choose the
Configuration
tab of your RDS instance dashboard, and under
Master Credentials ARN
, choose
Manage in Secrets Manager
to open your managed master database secret in Secrets Manager.
-
In
MySQL Workbench , log in to your Amazon RDS database as the master database by using the credentials that you just retrieved from the secret. For more information, seeConnecting to a DB instance running the MySQL database engine . -
For the master database, create a new database user with the permissions that you want by running the following SQL command. Make sure to replace
<password>
with your own information, and make sure to use a strong password.
CREATE USER 'child'@'%' IDENTIFIED by <password> ;
For more information about creating users, see the
Set up alternating users rotation for the new database user
In this section, you will learn how to use the master database credential to set up multi-user rotation for application credentials.
To set up alternating users rotation
-
In the
Secrets Manager console , under Secrets , choose Store a new secret . - For Secret type , select Credentials for Amazon RDS database .
- In the Credentials section, enter the username and password of the new database user.
-
In the
Database
section, select your Amazon RDS instance, and then choose
Next
, as shown in Figure 5.
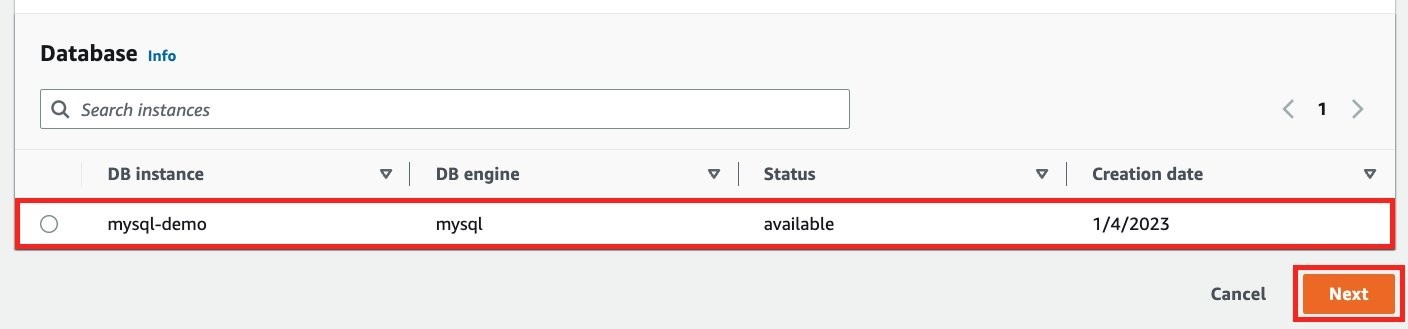
Figure 5: Select the RDS instance
- On the Configure secret page, give the secret a name and description. No other configuration is needed.
-
On the
Configure rotation – optional
page, turn on
Automatic rotation
.
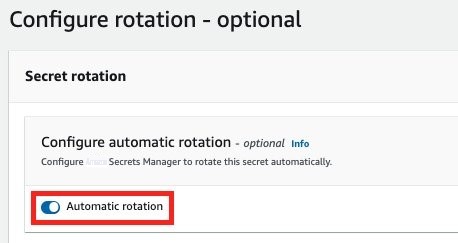
Figure 6: Select automatic rotation
- In the Rotation schedule section, configure the rotation schedule according to your needs.
-
In the
Rotation function
section, do the following:
- Enter a descriptive name for the Lambda function that will be created.
- For Use separate credentials to rotate this secret , select Yes .
-
For
Secrets
, choose the master database secret that was created by Amazon RDS.
Note : To find the name of your master database secret, in the Amazon RDS console, on your Amazon RDS instance details page, choose the Configuration tab and then see the Master Credentials ARN .
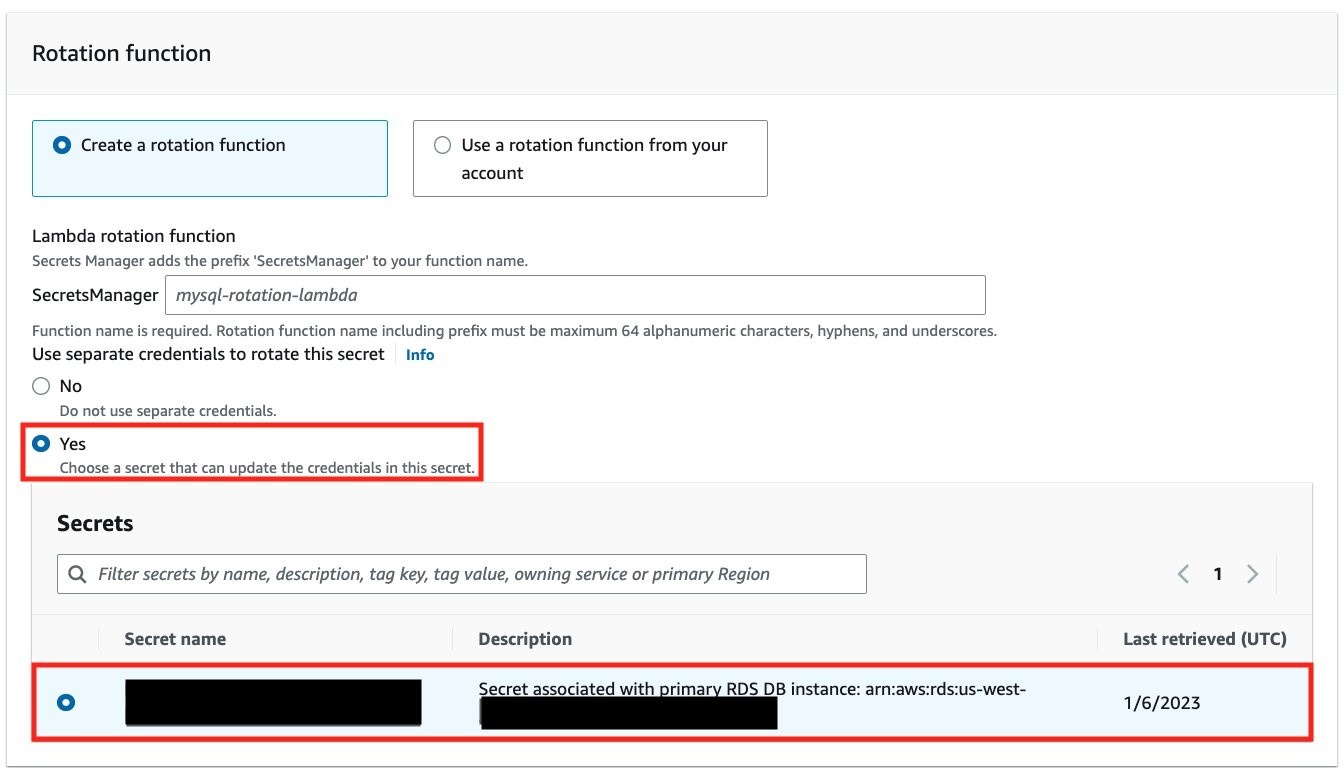
Figure 7: Select separate credentials for rotation
- Choose Next , and then on the Review page, choose Store .
It will take a few minutes for the Secrets Manager workflow to set up the rotation Lambda function before the new database user secret is ready to be rotated.
To check that rotation is enabled
-
In the Secrets Manager console, navigate to the new database user secret.
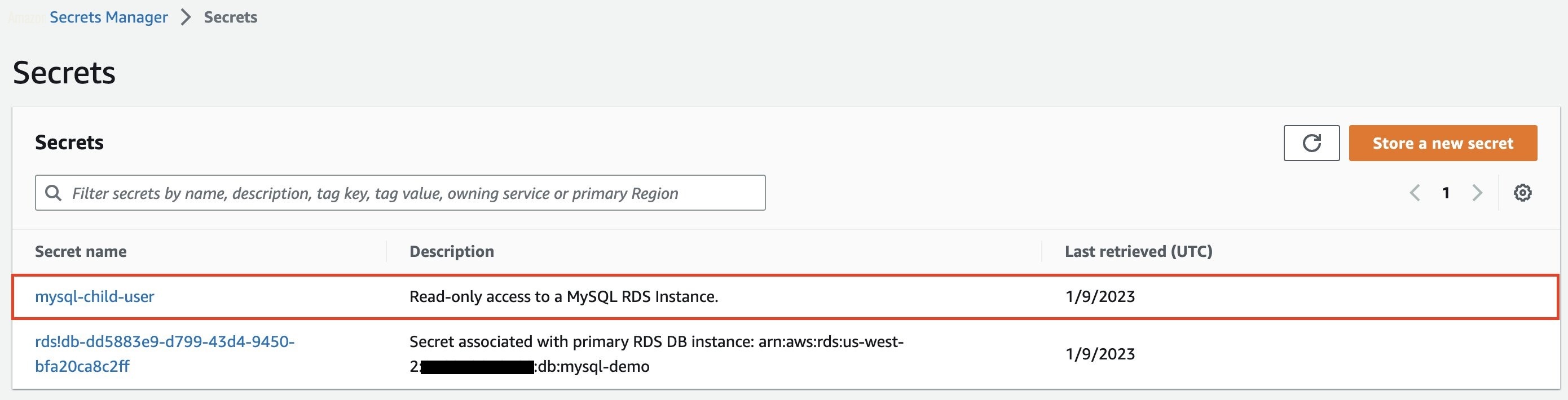
Figure 8: View the child secret
-
In the
Rotation configuration section
, verify that
Rotation status
is
Enabled
.
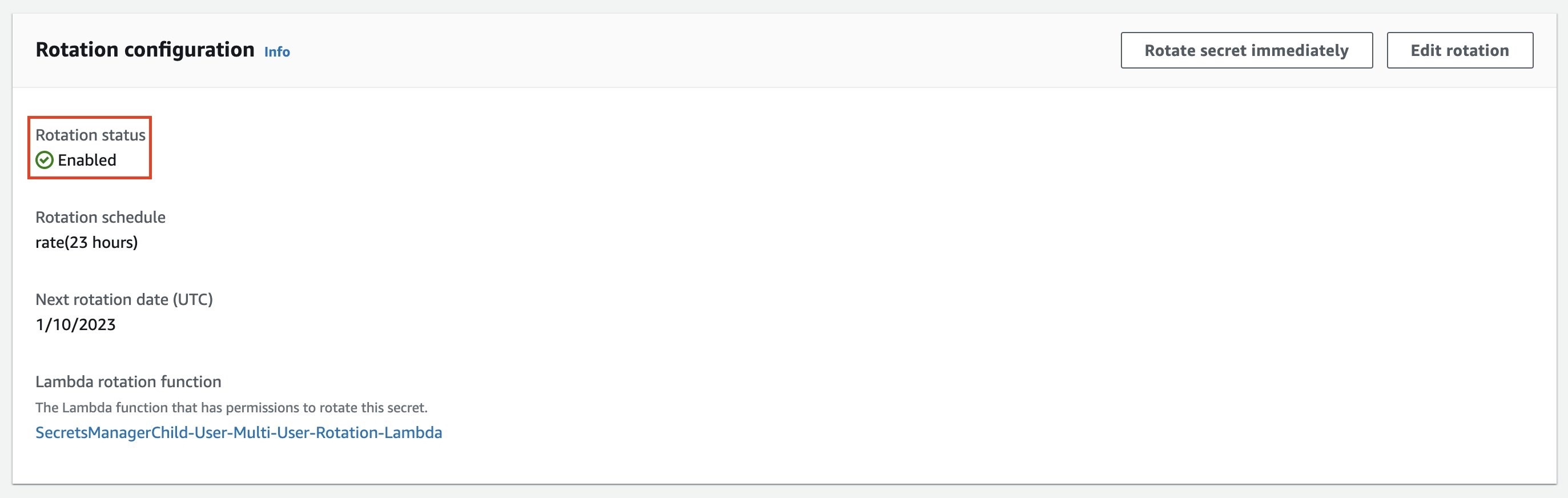
Figure 9: Verify the rotation status
For more details and troubleshooting on this process, see
Clean up the resources
By deleting the Amazon RDS instance, you will automatically clean up the managed master database credential secret.
To delete the Amazon RDS instance
-
Open the
Amazon RDS console . - From the navigation pane, choose Databases and then select the DB cluster to be modified.
- Choose Actions , and then choose Modify Cluster .
- Choose Disable deletion protection , and then choose Continue .
- Choose Apply immediately .
- From the Actions dropdown, choose Delete .
-
(Optional) Use the menu to create final snapshots or automated backups of your Amazon RDS instance.
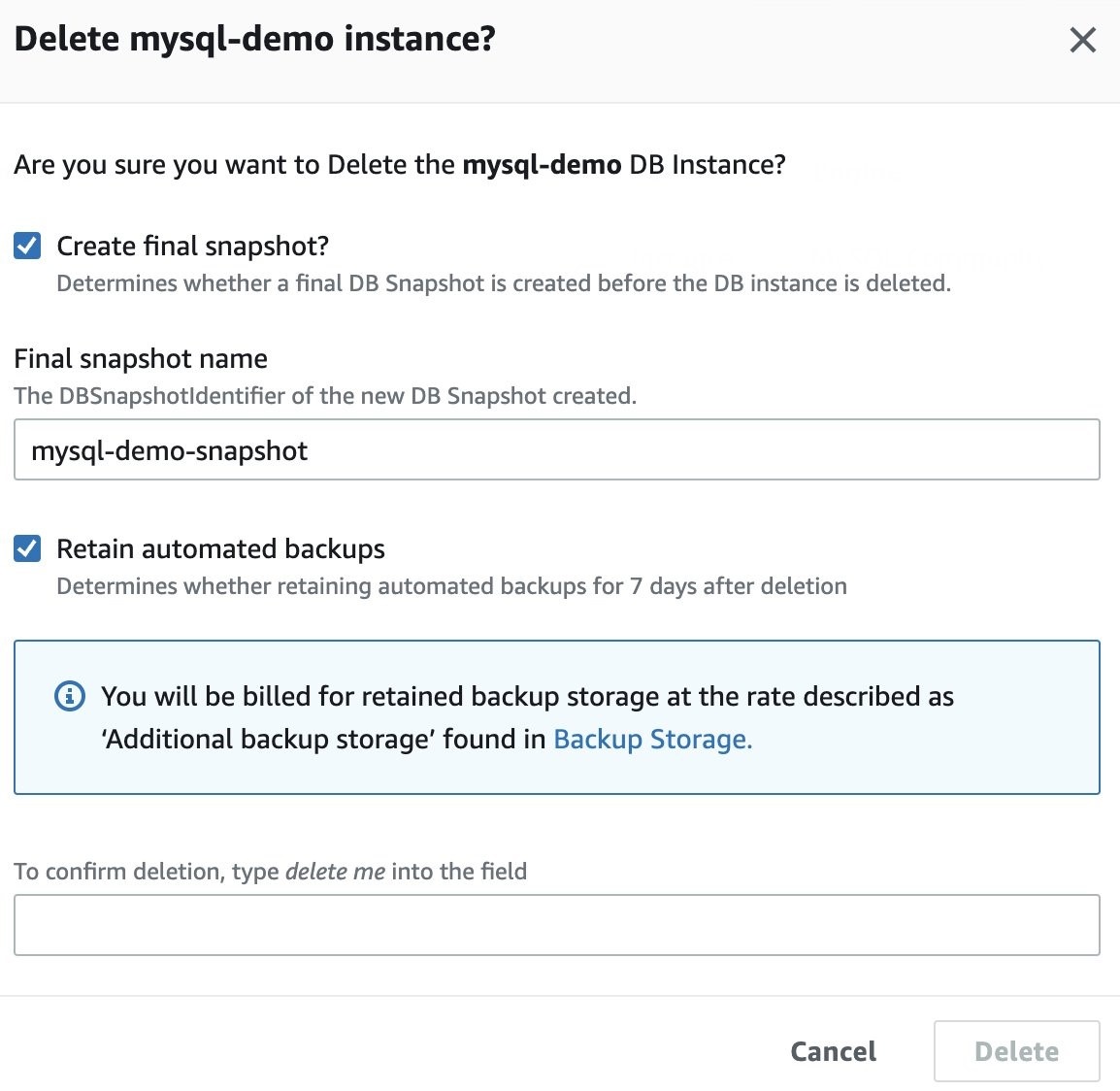
Figure 10: Create snapshots and backups
- When you’re ready, enter delete me .
For more information, see
To clean up alternating users rotation on the new database user secret
-
In the
Secrets Manager console , open the new database user secret.
Figure 11: Select child secret
-
In the
Rotation configuration
section, choose the Lambda rotation function.
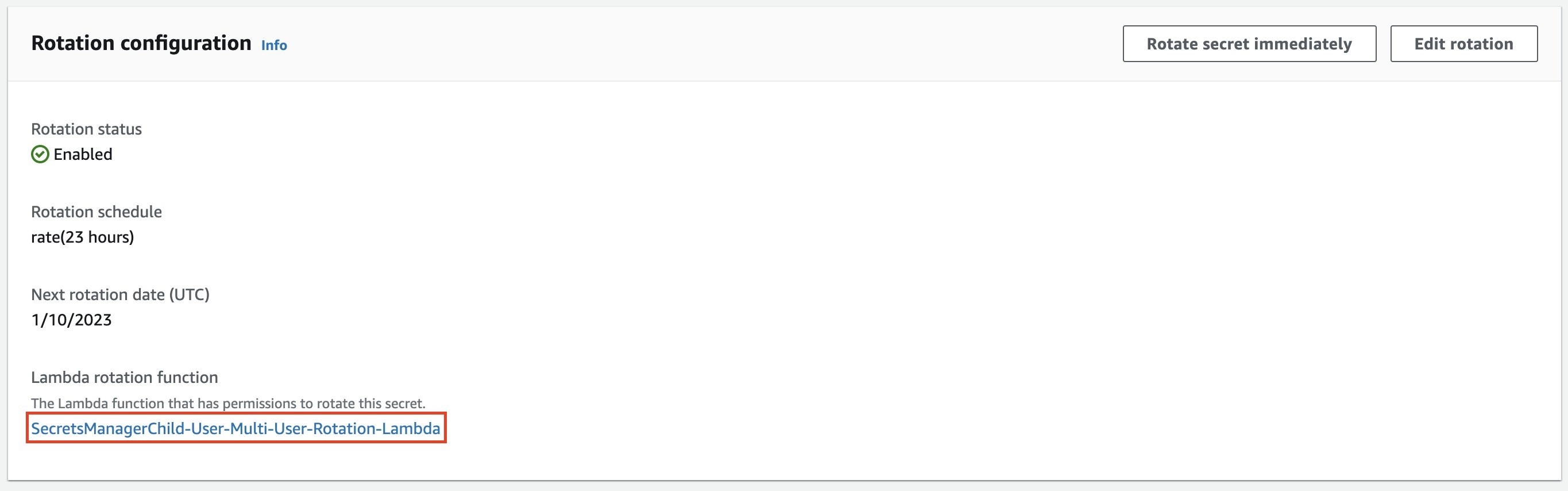
Figure 12: View the rotation function
-
In the Lambda console, under
Application
, select the application.
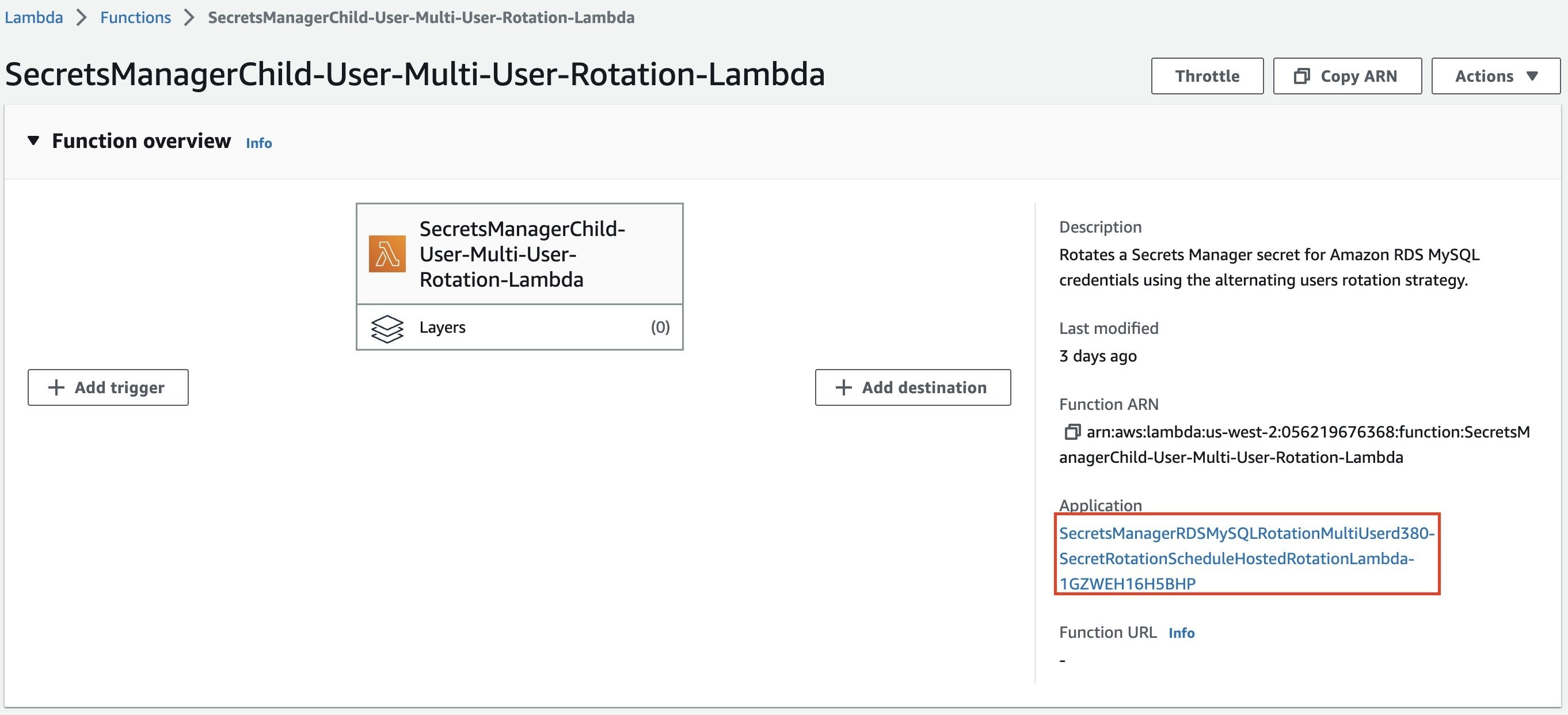
Figure 13: Open application
- On the Deployments tab, choose CloudFormation stack .
-
Choose
Delete
and then follow the
Delete
menu steps. You might need to navigate to the root stack and choose
Delete
again. You might also need to disable termination protection for the stack. The console will guide you through that.
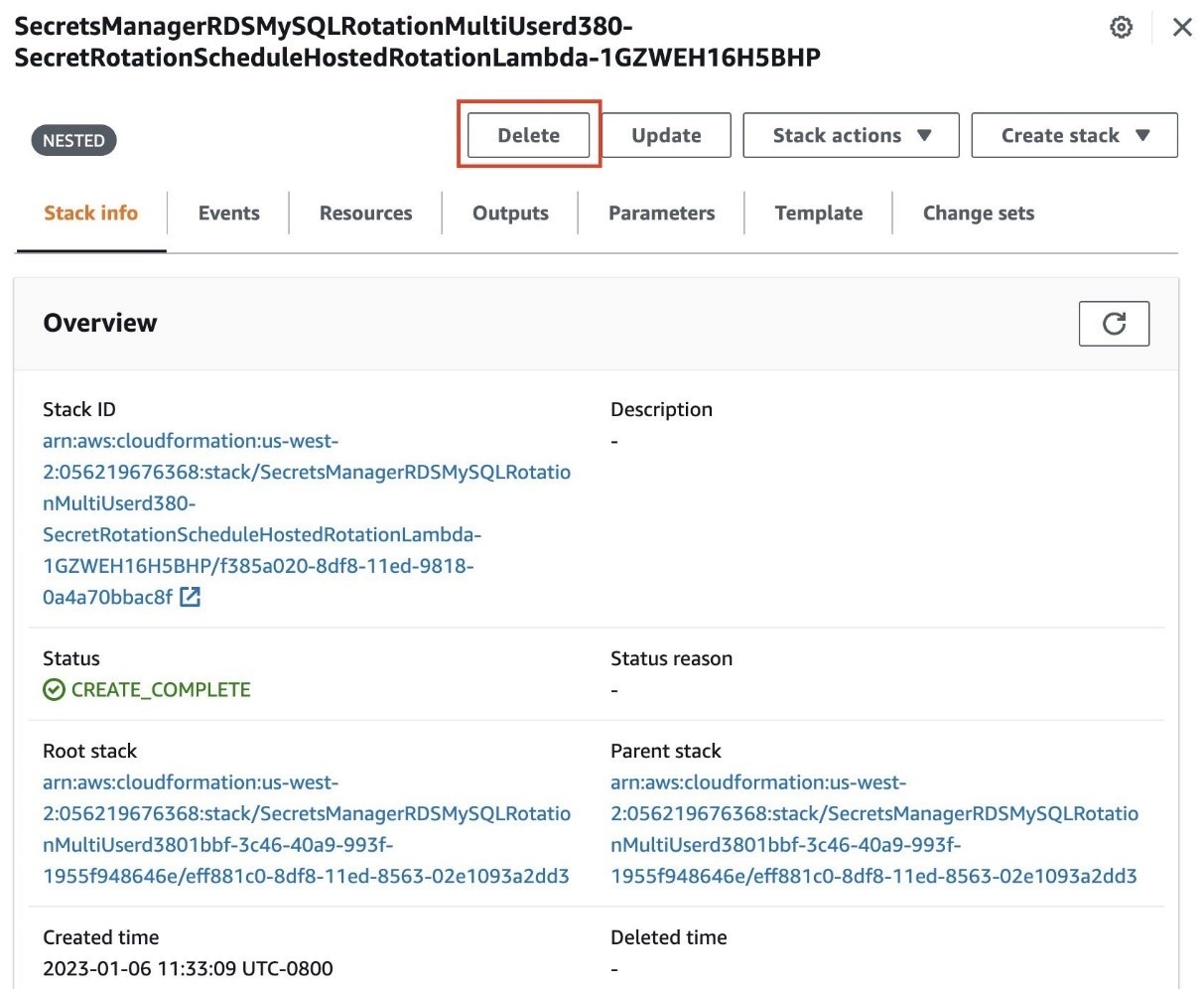
Figure 14: Choose delete
- Now that you have cleaned up rotation for the new database user secret, you need to delete the child secret. Navigate to the Secrets Manager console and select the secret that you want to delete.
-
In the
Actions
dropdown, select
Delete secret
to delete the secret.
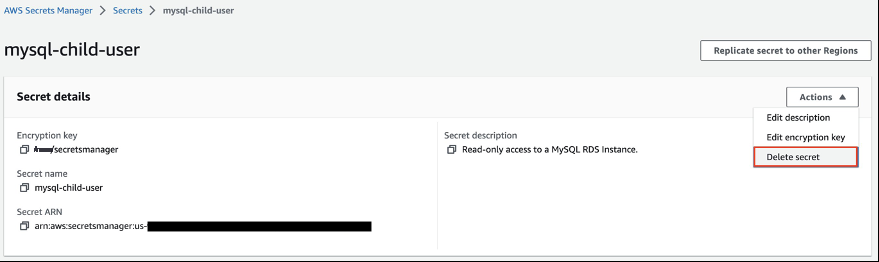
Figure 15: Delete child secret
Summary
Amazon RDS integration with Secrets Manager helps you better secure and manage master DB credentials. This integration helps you store the credentials when the DB instances are created and eliminates the effort for you to set up credential rotation.
In this blog post, you learned how to do the following:
- Set up an Amazon RDS instance that uses Secrets Manager to store the master database credentials
- View the credentials in Secrets Manager and confirm that rotation is set up
- Use the master database credentials to create database user credentials
- Set up alternating users rotation on database user credentials
Additional resources
For instructions on how to create database users for other Amazon RDS engine types, see the following resources:
-
PostgreSQL -
MariaDB -
Microsoft SQL Server -
Oracle -
Secrets Manager JDBC Library
If you have feedback about this post, submit comments in the
Comments
section below. If you have questions about this post,
Want more Amazon Web Services Security news? Follow us on
The mentioned AWS GenAI Services service names relating to generative AI are only available or previewed in the Global Regions. Amazon Web Services China promotes AWS GenAI Services relating to generative AI solely for China-to-global business purposes and/or advanced technology introduction.