- Products›
- Amazon RDS›
- Amazon RDS features
Amazon RDS Security
overview
Amazon RDS is a managed relational database service that provides you six familiar database engines to choose from, including Amazon Aurora, MySQL, MariaDB, PostgreSQL, Oracle, and Microsoft SQL Server.
Amazon RDS and Amazon Aurora provide a set of features to ensure that your data is securely stored and accessed. Run your database in Amazon Virtual Private Cloud (VPC) for network-level isolation. Use security groups to control what IP addresses or Amazon EC2 instances can connect to your databases. This built-in firewall prevents any database access except through rules you specify.
Use Amazon Identity and Access Management (IAM) policies to assign permissions that determine who is allowed to manage RDS resources. Use the security features of your database engine to control who can log in to the databases, just as you do if the database was on your local network. You can also map database users to IAM roles for federated access.
Use Secure Socket Layer / Transport Layer Security (SSL/TLS) connections to encrypt data in transit. Encrypt your database storage and backups at rest using Amazon Key Management Service (KMS). Monitor database activity and integrate with partner database security applications with Database Activity Streams.
Page topics
FAQS
Open allAmazon RDS encrypts your databases using keys you manage with the Amazon Key Management Service (KMS). On a database instance running with Amazon RDS encryption, data stored at rest in the underlying storage is encrypted, as are its automated backups, read replicas, and snapshots. RDS encryption uses the industry standard AES-256 encryption algorithm to encrypt your data on the server that hosts your RDS instance.
Amazon RDS also supports Transparent Data Encryption (TDE) for SQL Server (SQL Server Enterprise Edition) and Oracle (Oracle Advanced Security option in Oracle Enterprise Edition).
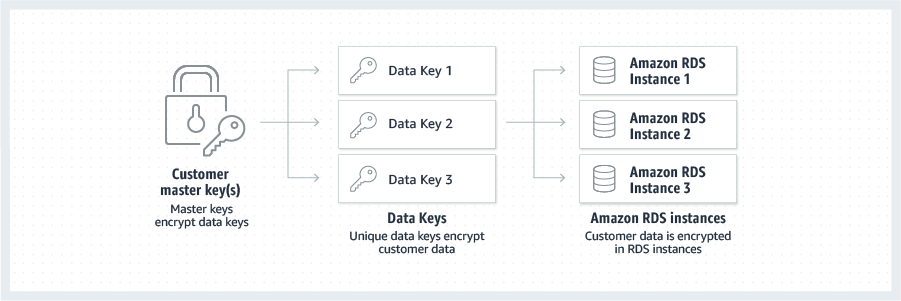
Best practice recommendations
Amazon RDS provide best practice guidance by analyzing configuration and usage metrics from your database instances. Recommendations cover areas such as security, encryption, IAM and VPC. You can browse the available recommendations and perform a recommended action immediately, schedule it for their next maintenance window, or dismiss it entirely.
Encrypt communications between your application and your DB Instance using SSL/TLS. Amazon RDS creates an SSL certificate and installs the certificate on the DB instance when the instance is provisioned. For MySQL, you launch the mysql client using the --ssl_ca parameter to reference the public key in order to encrypt connections. For SQL Server, download the public key and import the certificate into your Windows operating system. RDS for Oracle uses Oracle native network encryption with a DB instance. You simply add the native network encryption option to an option group and associate that option group with the DB instance. Once an encrypted connection is established, data transferred between the DB Instance and your application will be encrypted during transfer. You can also require your DB instance to only accept encrypted connections.
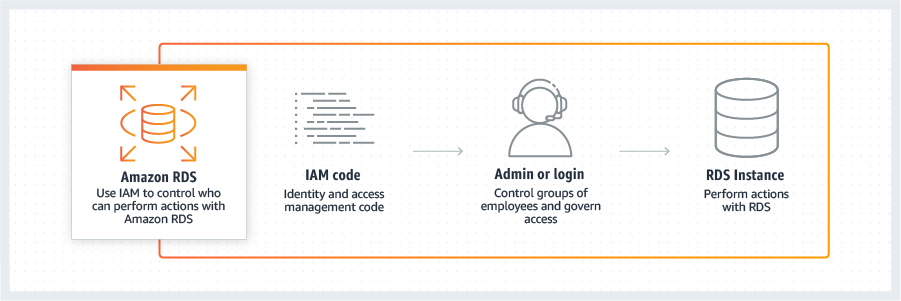
Amazon RDS is integrated with Amazon Identity and Access Management (IAM) and provides you the ability to control the actions that your Amazon IAM users and groups can take on specific resources (e.g., DB Instances, DB Snapshots, DB Parameter Groups, DB Event Subscriptions, DB Options Groups). In addition, you can tag your resources, and control the actions that your IAM users and groups can take on groups of resources that have the same tag (and tag value). For more information about IAM integration, see the IAM Database Authentication documentation.
You can also tag your Amazon RDS resources and control the actions that your IAM users and groups can take on groups of resources that have the same tag and associated value. For example, you can configure your IAM rules to ensure developers are able to modify "Development" database instances, but only Database Administrators can make changes to "Production" database instances.
When you first create a DB Instance within Amazon RDS, you will create a master user account, which is used only within the context of Amazon RDS to control access to your DB Instance(s). The master user account is a native database user account that allows you to log on to your DB Instance with all database privileges. You can specify the master user name and password you want associated with each DB Instance when you create the DB Instance. Once you have created your DB Instance, you can connect to the database using the master user credentials. Subsequently, you can create additional user accounts so that you can restrict who can access your DB Instance.
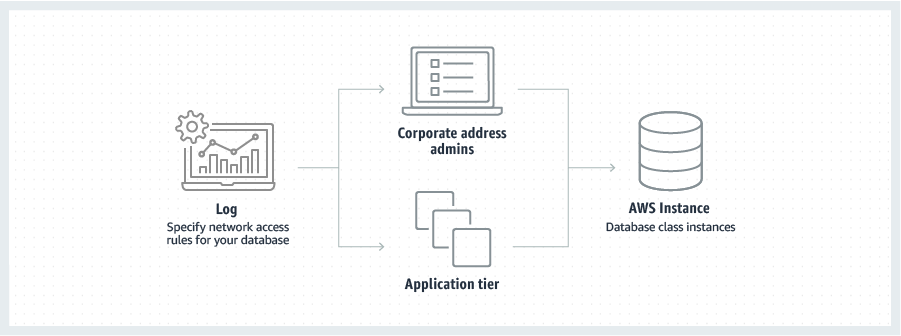
Using Amazon Virtual Private Cloud (VPC), you can isolate your DB Instances in your own virtual network, and connect to your existing IT infrastructure using Direct Connect.
Amazon VPC enables you to isolate your DB Instances by specifying the IP range you wish to use. Running Amazon RDS in a VPC enables you to have a DB instance within a private subnet. You can also set up a virtual private gateway that extends your corporate network into your VPC, and allows access to the RDS DB instance in that VPC. Refer to the Amazon VPC User Guide for more details. DB Instances deployed within an Amazon VPC can be accessed from the Internet or from Amazon EC2 Instances outside the VPC via VPN or bastion hosts that you can launch in your public subnet. To use a bastion host, you will need to set up a public subnet with an EC2 instance that acts as a SSH Bastion. This public subnet must have an Internet gateway and routing rules that allow traffic to be directed via the SSH host, which must then forward requests to the private IP address of your Amazon RDS DB instance. DB Security Groups can be used to help secure DB Instances within an Amazon VPC. In addition, network traffic entering and exiting each subnet can be allowed or denied via network ACLs.
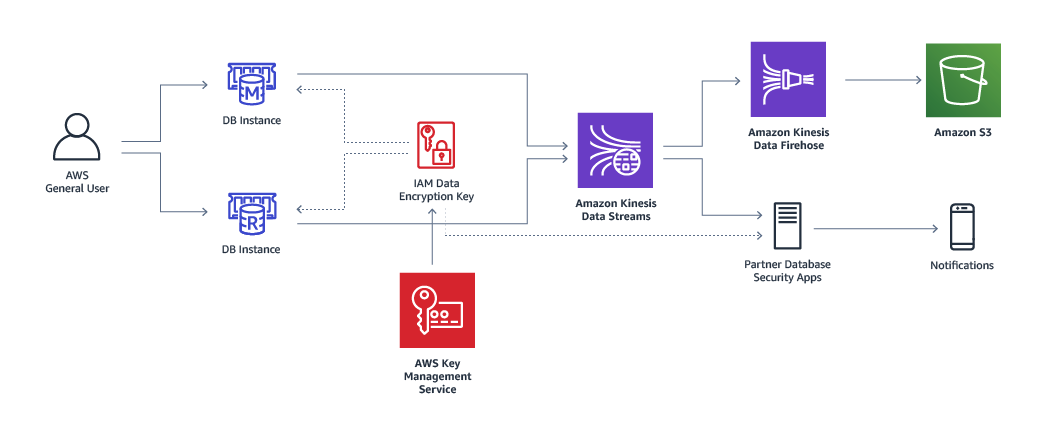
Beyond external security threats, managed databases need to provide protection against insider risks from database administrators (DBAs). Database Activity Streams, currently supported for Amazon Aurora, provides a real-time data stream of the database activity in your relational database. When integrated with 3rd party database activity monitoring tools, you can monitor and audit database activity to provide safeguards for your database and meet compliance and regulatory requirements.
Database Activity Streams protects your database from internal threats by implementing a protection model that controls DBA access to the database activity stream. Thus the collection, transmission, storage, and subsequent processing of the database activity stream is beyond the access of the DBAs that manage the database.
The stream is pushed to an Amazon Kinesis data stream that is created on behalf of your database. From Kinesis Data Firehose, the database activity stream can then be consumed by Amazon CloudWatch or by partner applications for compliance management. These partner applications can use the database activity stream information to generate alerts and provide auditing of all activity on your Amazon Aurora database.
You can learn more about using Database Activity Streams for the PostgreSQL- and MySQL-compatible editions of Aurora in the documentation page.
Amazon RDS is committed to offering customers a strong compliance framework and advanced tools and security measures that customers can use to evaluate meet, and demonstrate compliance with applicable legal and regulatory requirements.
For more information, please visit the Amazon Web Services Compliance Page.